Format String Vulnerabilities
Procedure
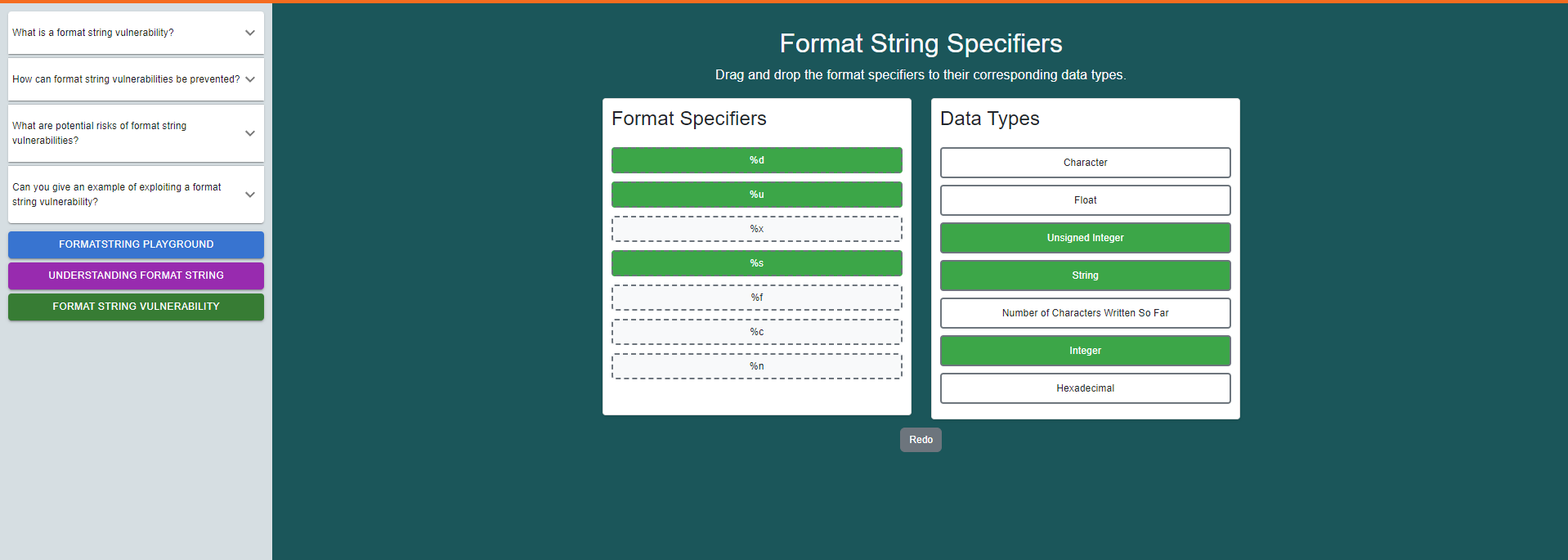
Click on the "Format String Playground" button.
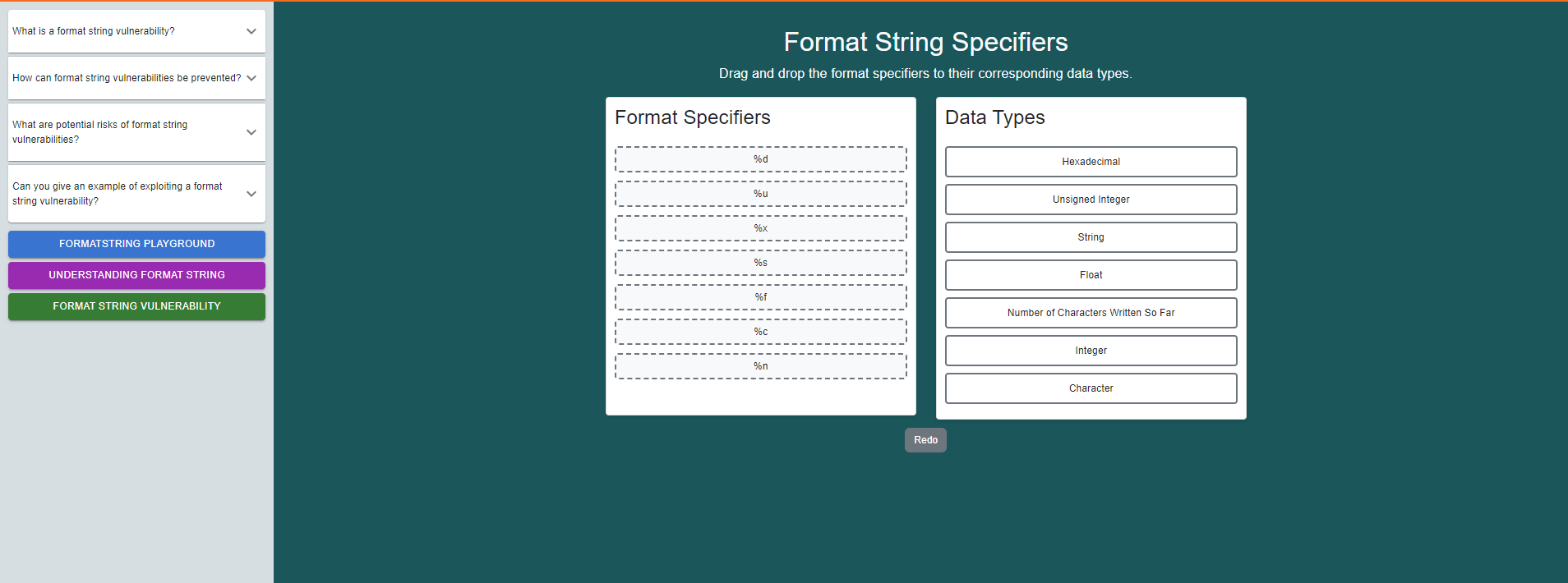
Drag and drop the format specifiers to their corresponding data types.
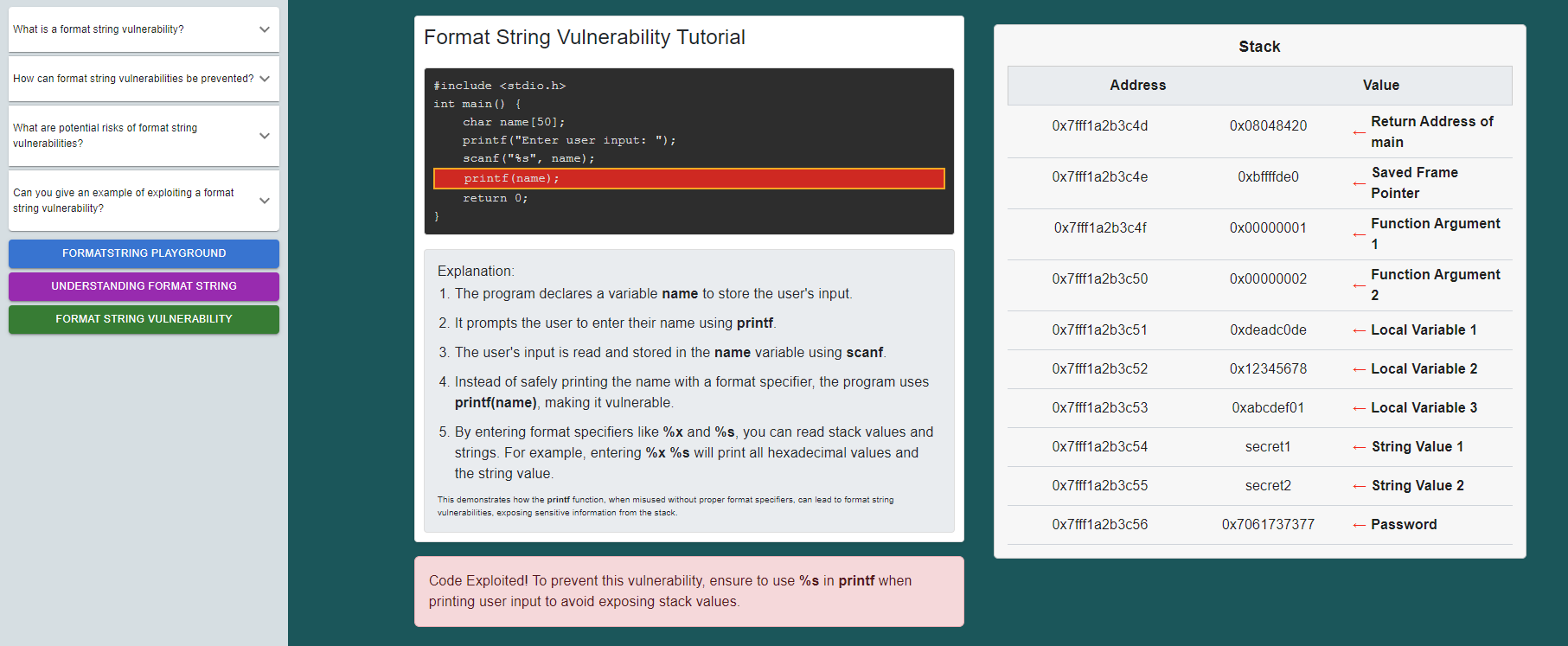
Click on the "Understanding Format String " button.
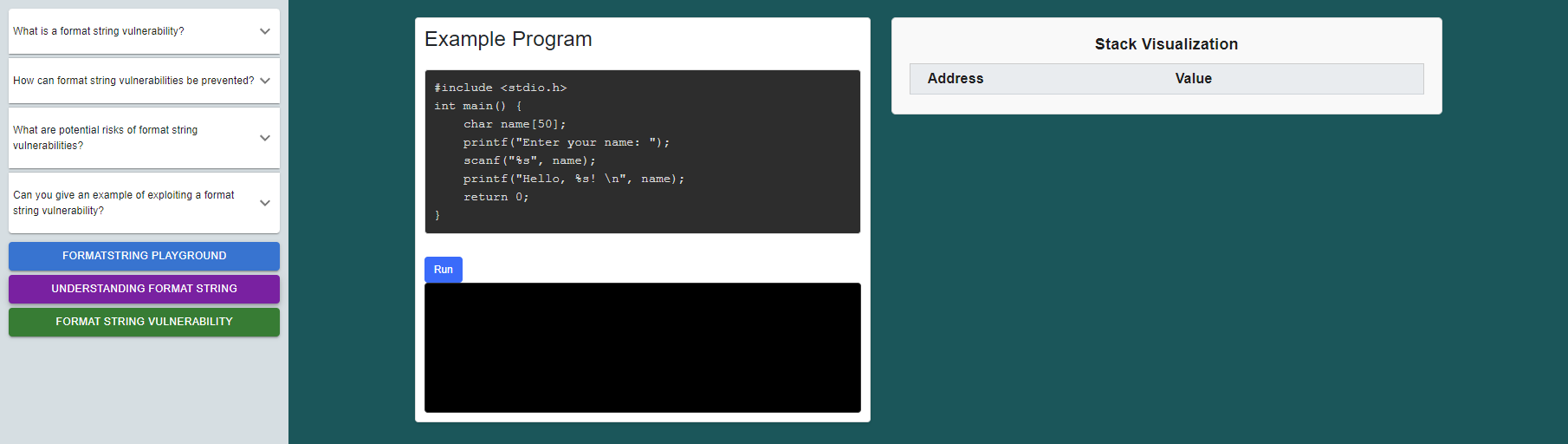
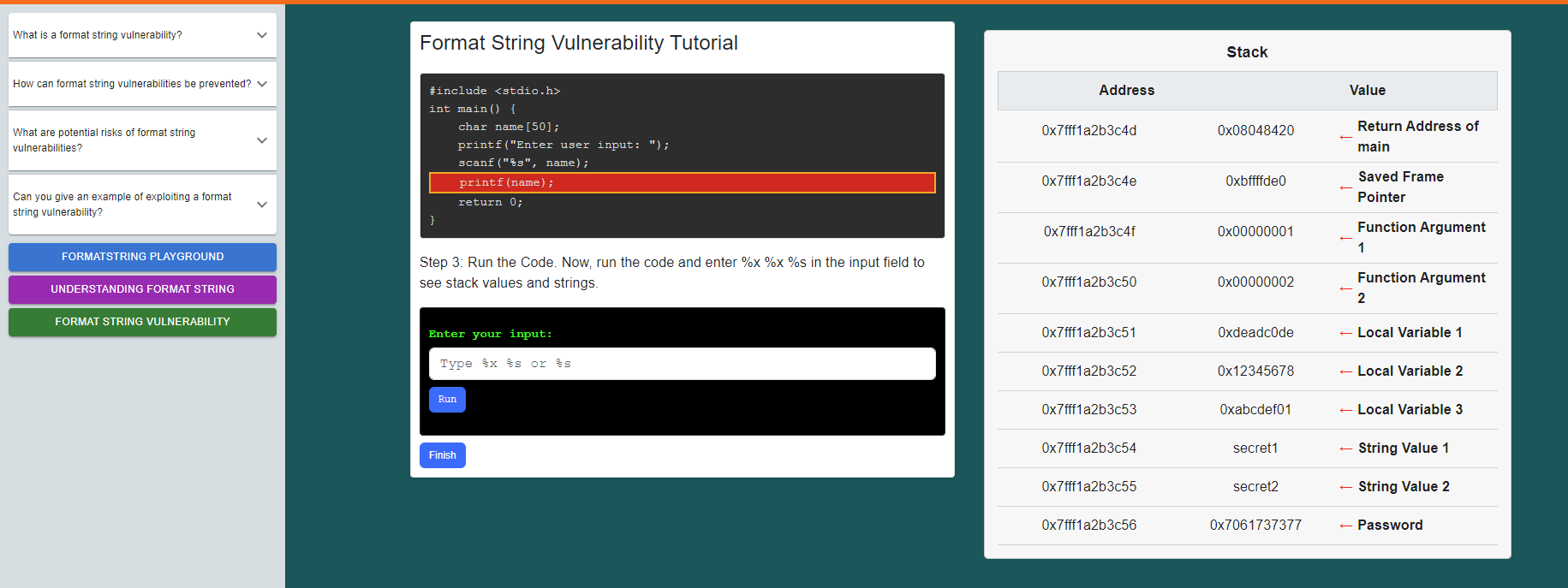
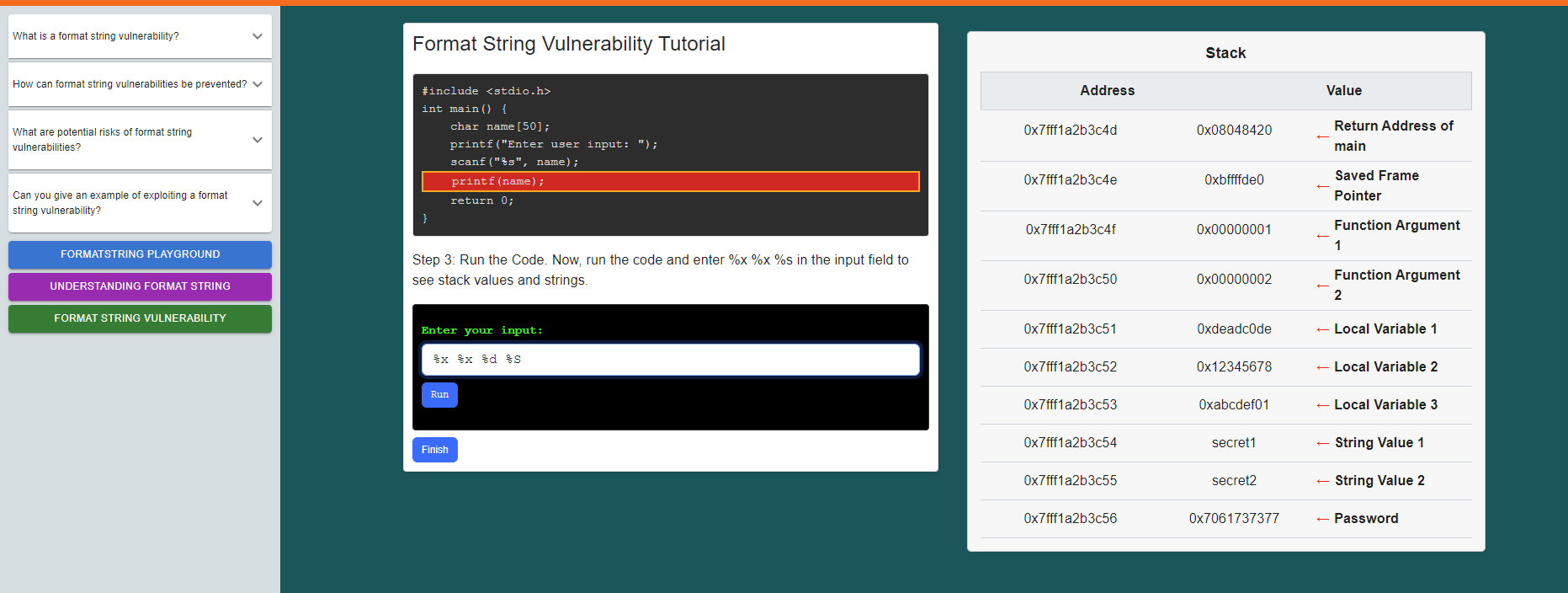
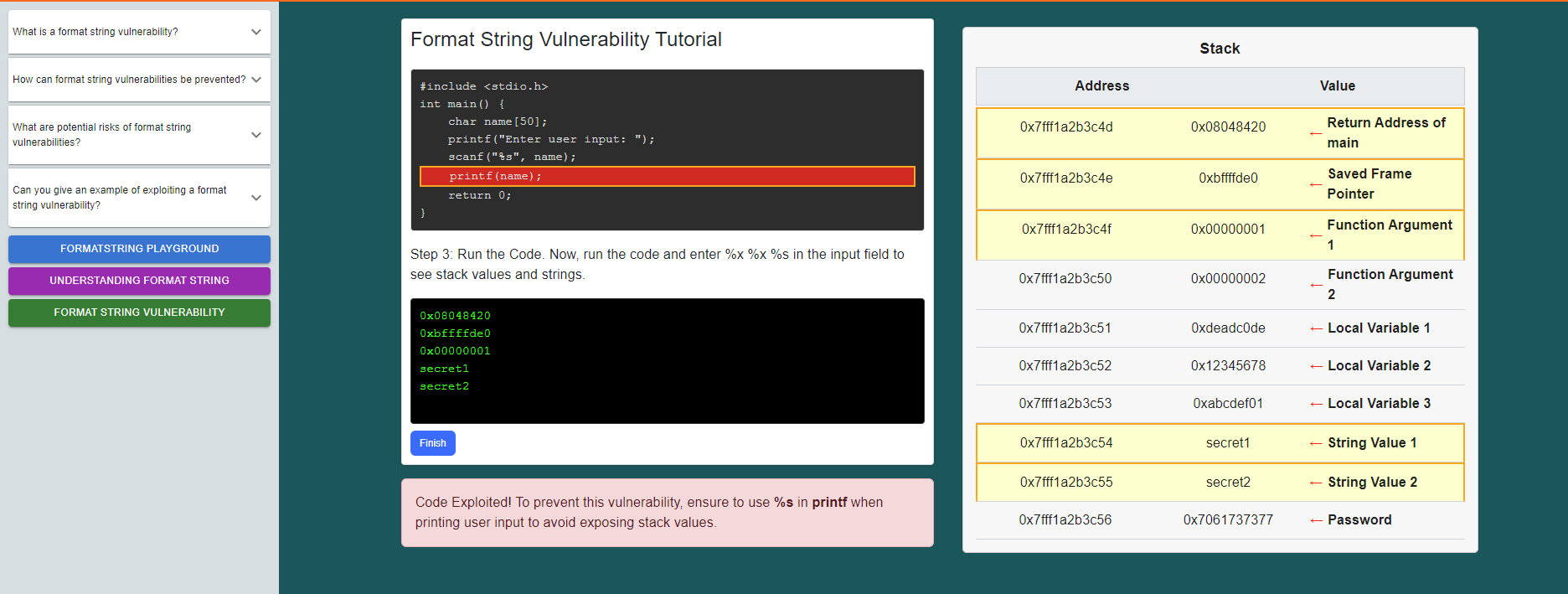
click on the run button also observe the explanation given below.
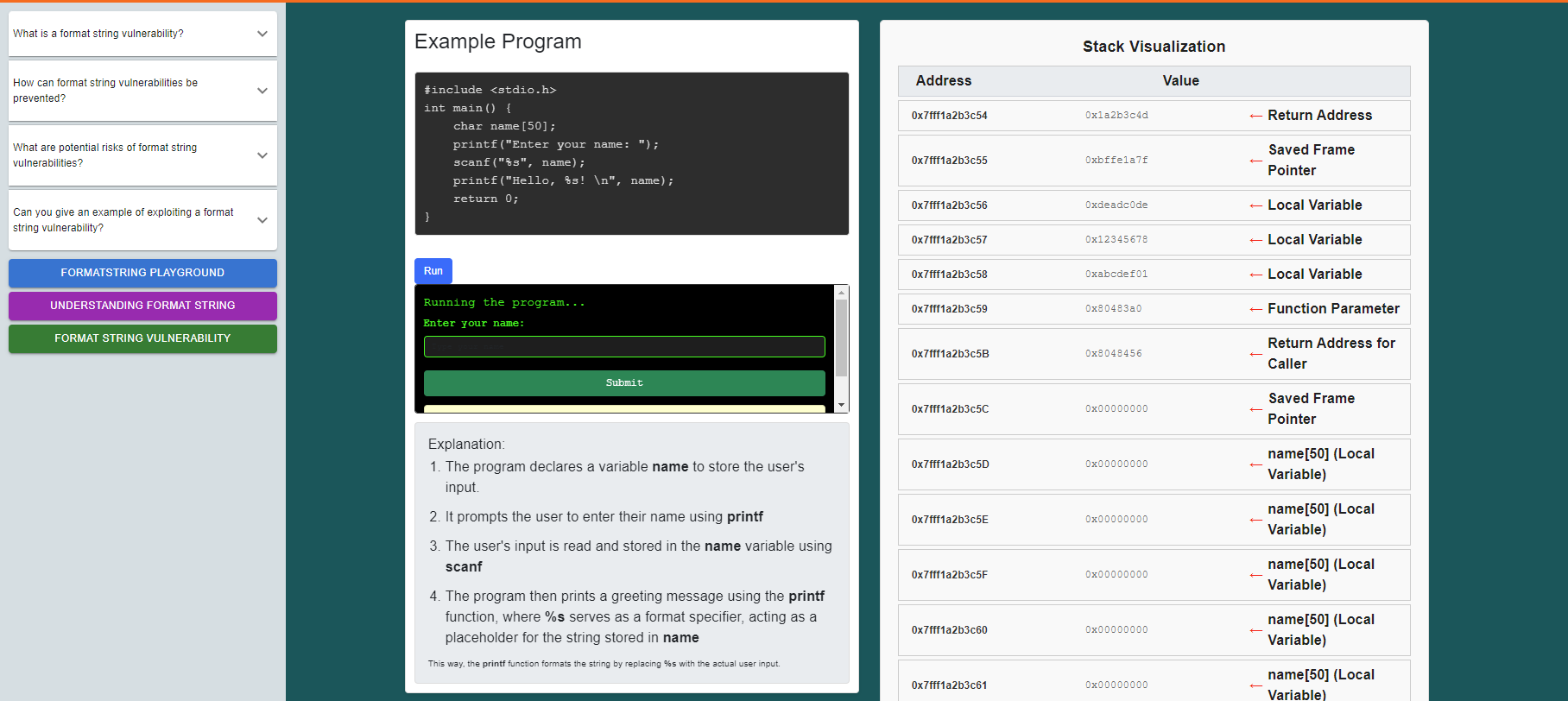
Enter your name, observe the stack visualization and the program's output to see how the value is stored in the stack, retrieved, and displayed as the output.
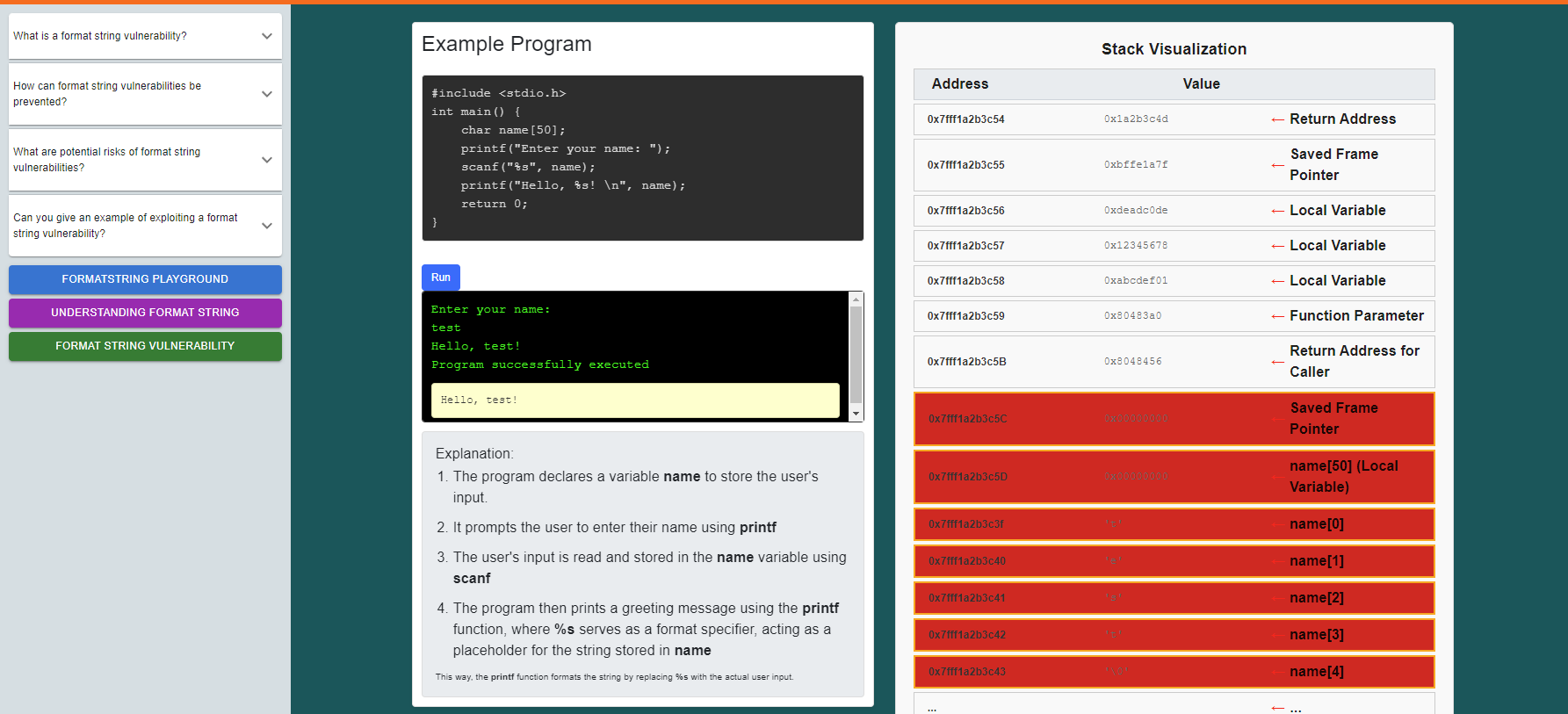
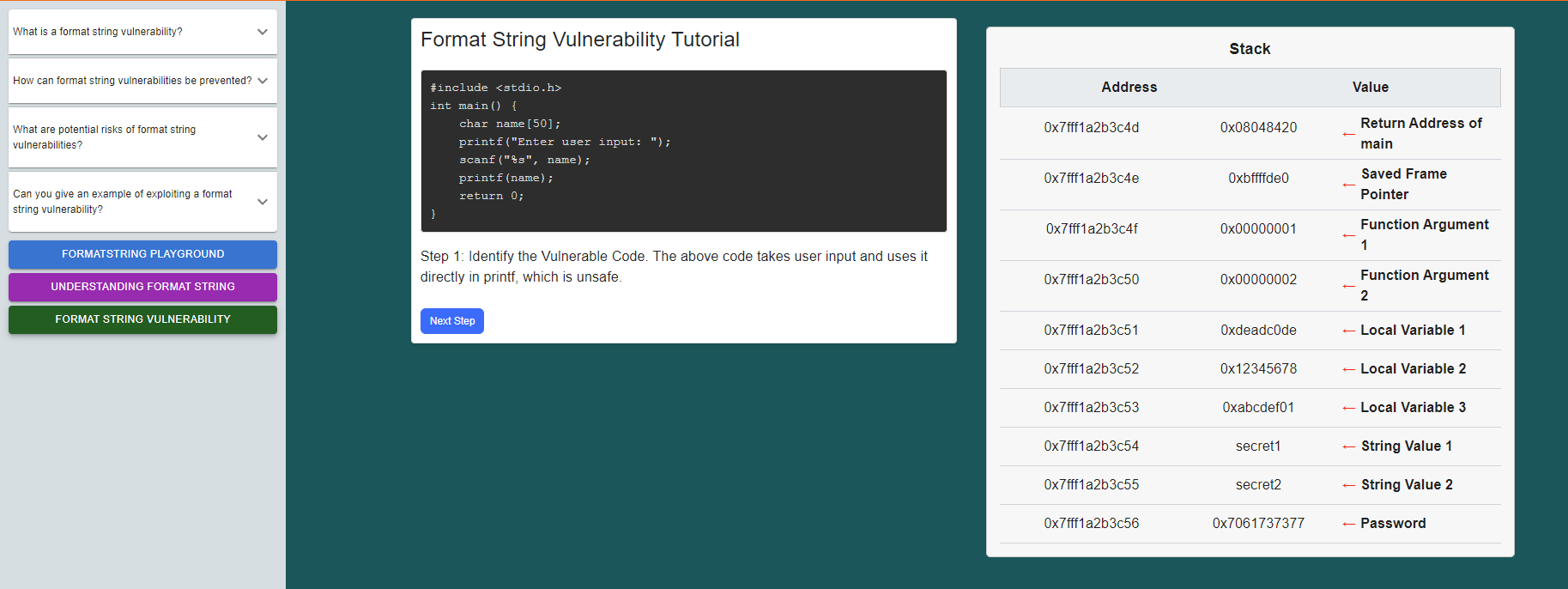
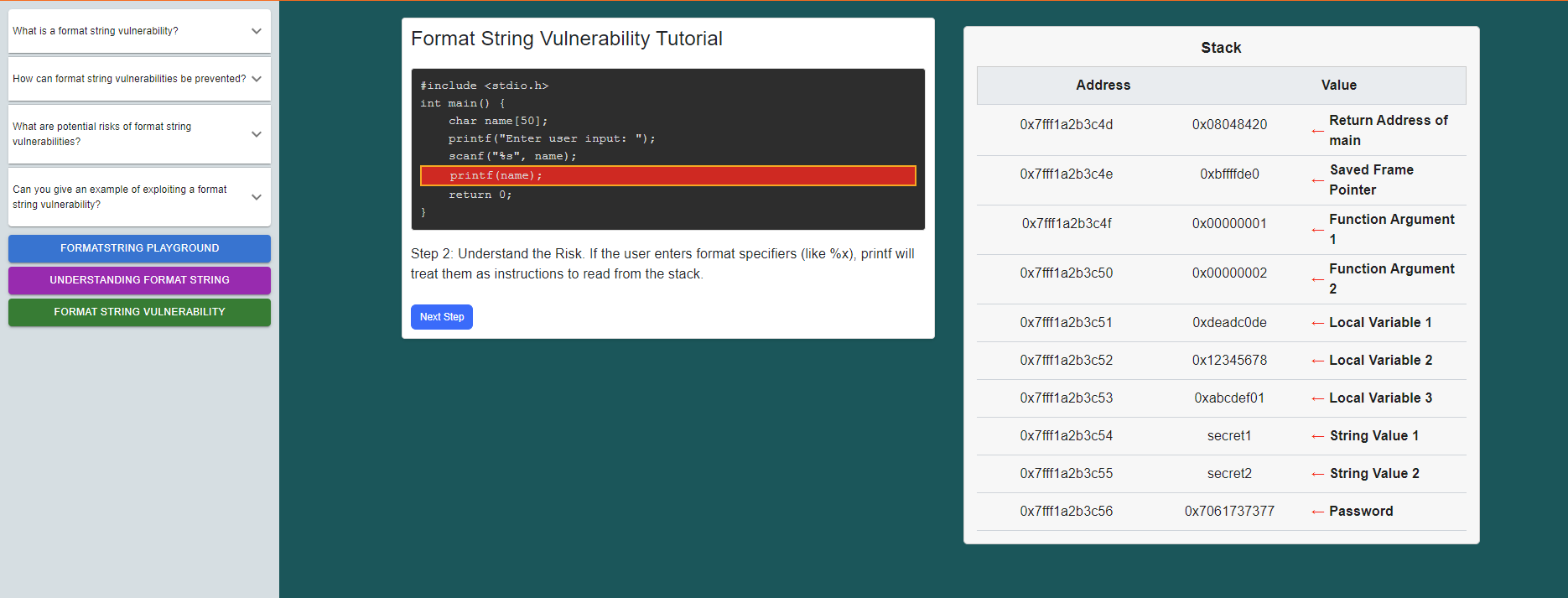
click on the "Format String Vulnerability" button
Follow the instructions given and observe how the vulnerability occurs.