Identifying and Investigating Various Network Attacks using Wireshark
Procedure
Wireshark is widely used by network administrators, security professionals, developers, and researchers for various purposes, including network troubleshooting, protocol analysis, security auditing, malware analysis, and network forensics.
Analyze incoming and outgoing packets (pcap files) and to understand different network attacks.
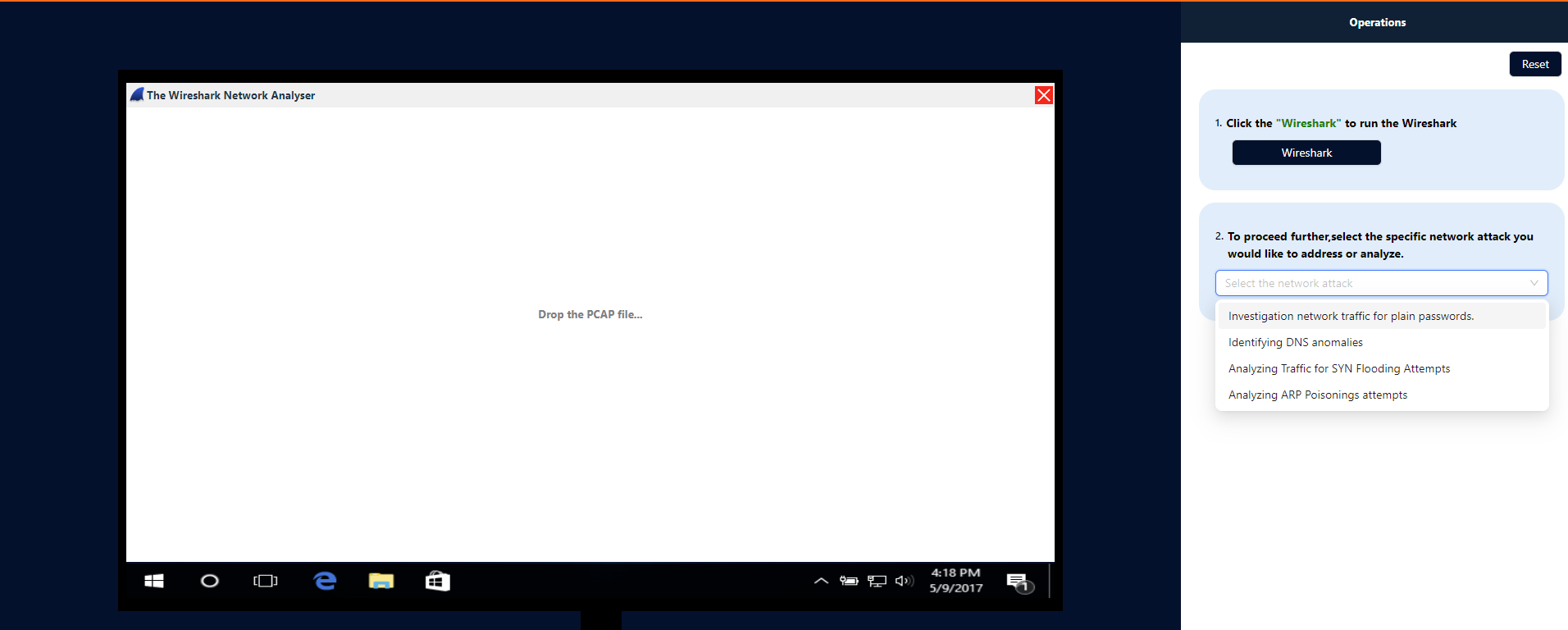
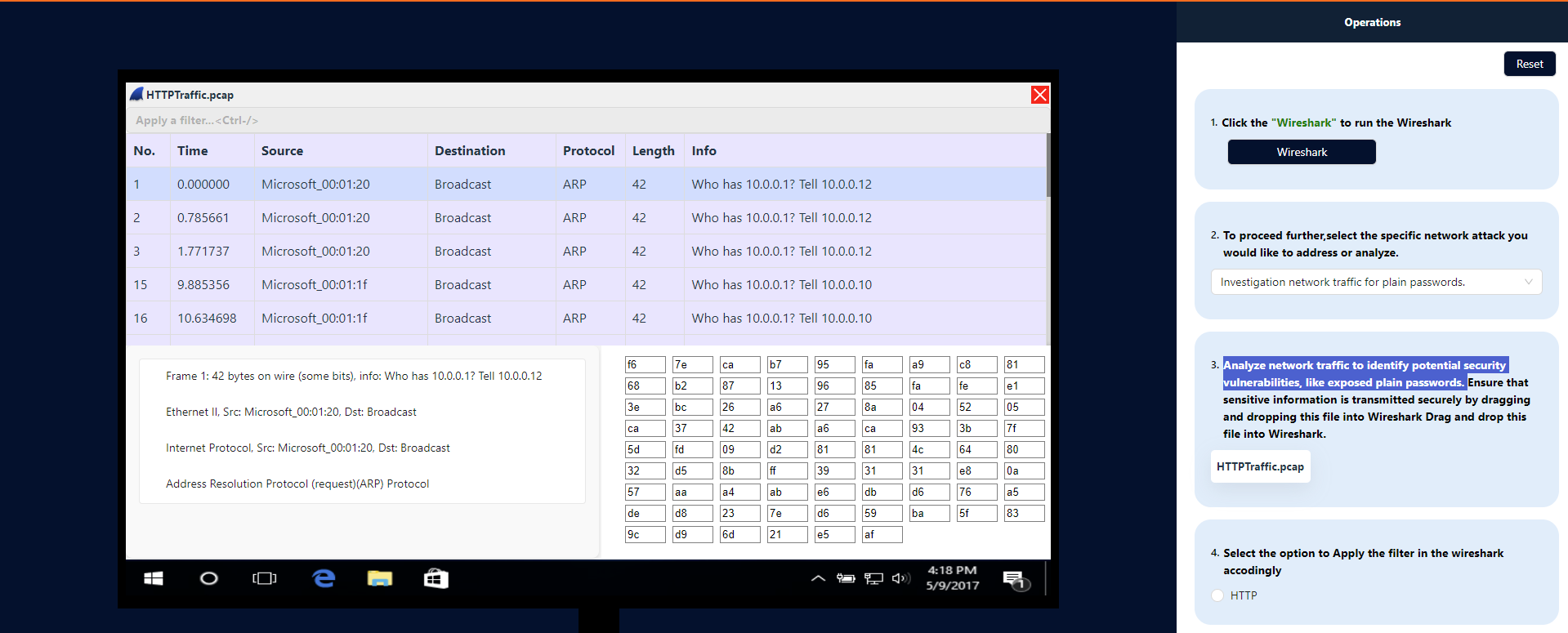
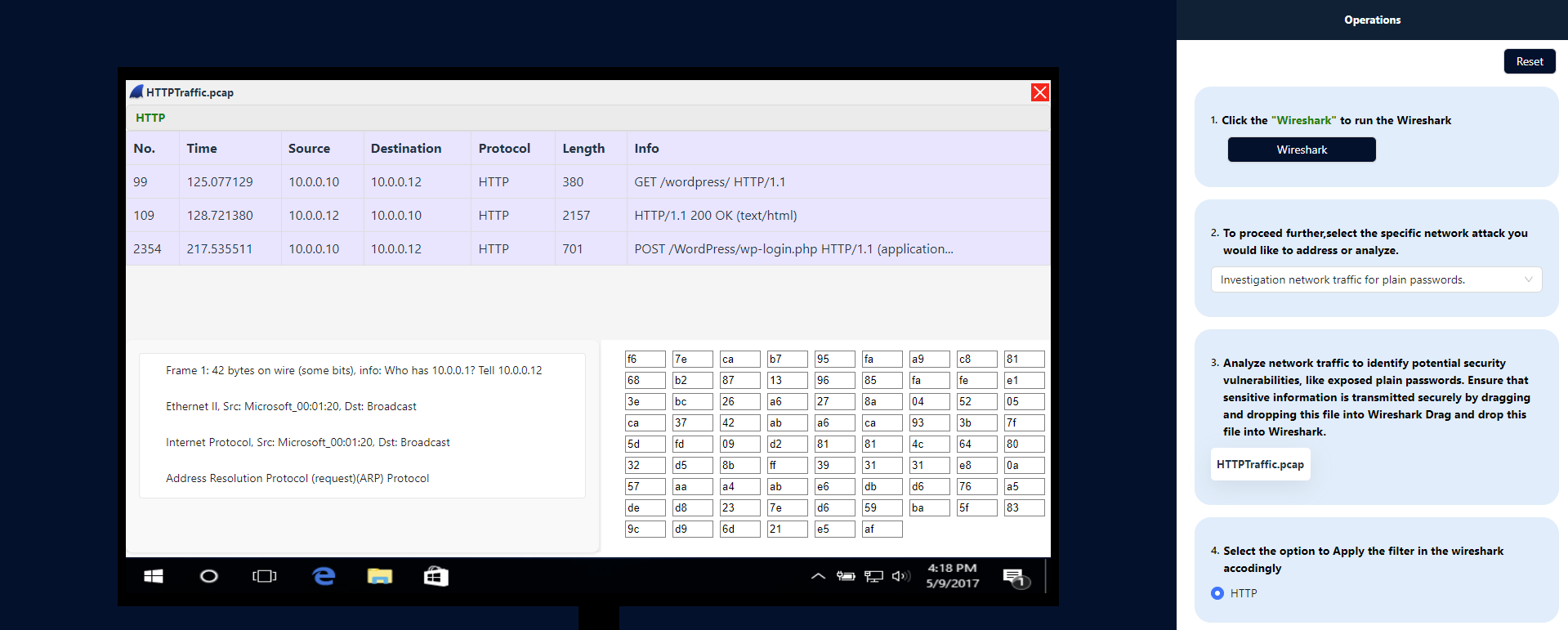
Similarly, choose the specific network attack you want to investigate or analyze,from (step2) and then repeat the process accordingly
