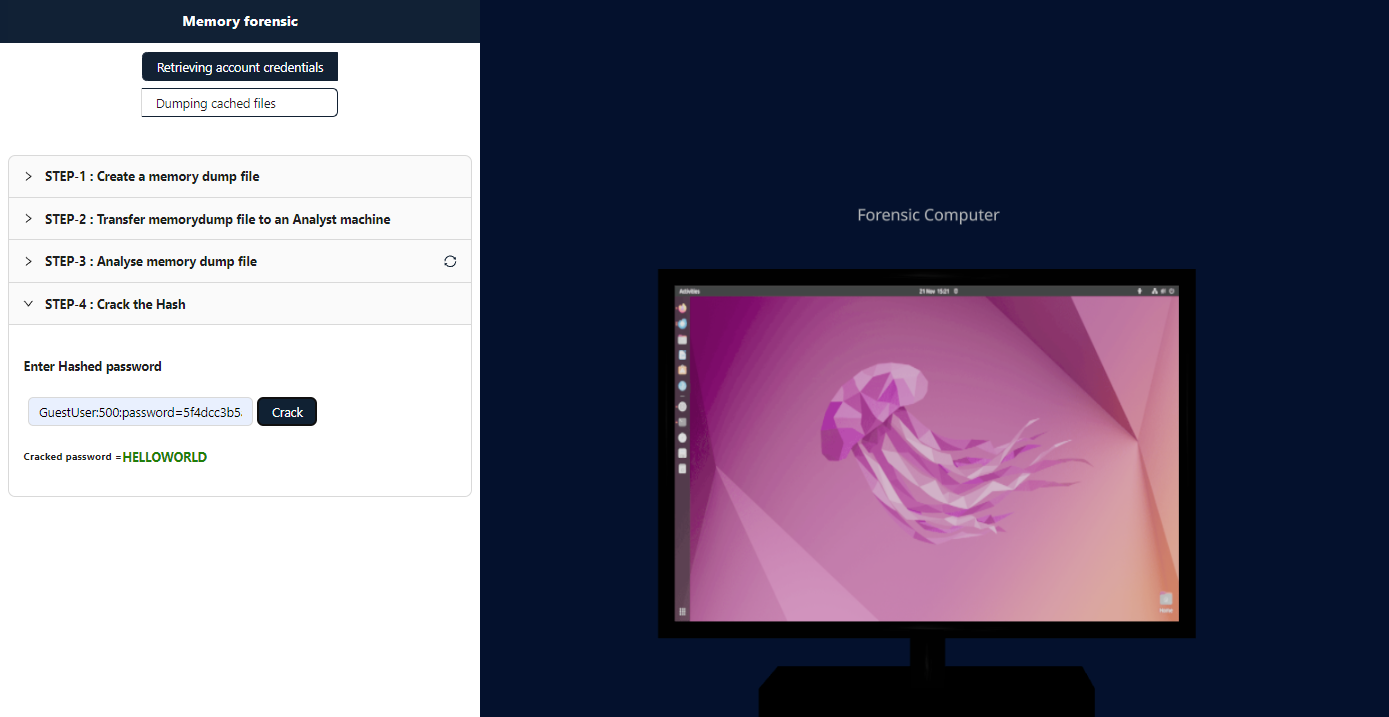
Retrieving Password Hashes and Dumping Cached Files from Memory Dumps
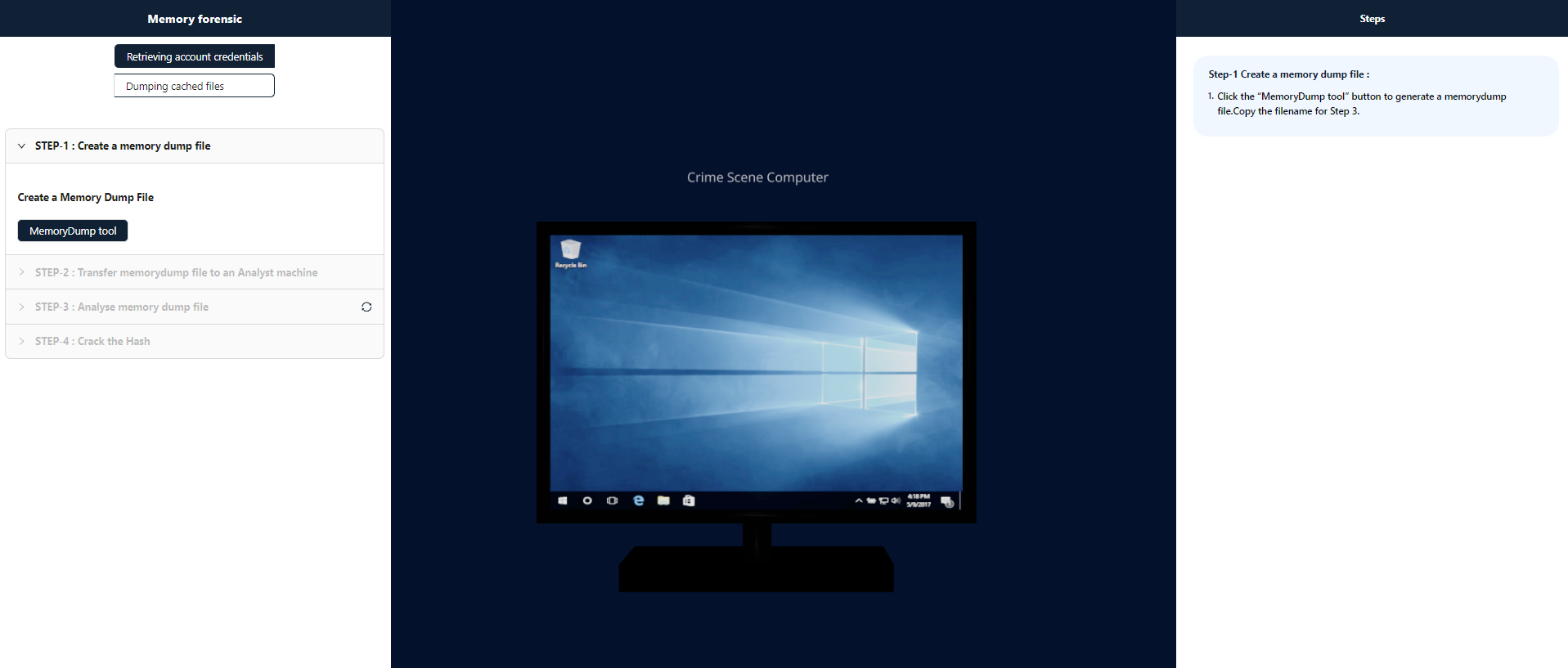
Step-1 Create a memory dump file :
Click the “MemoryDump tool” button to generate a memorydump file.Copy the filename for Step 3.
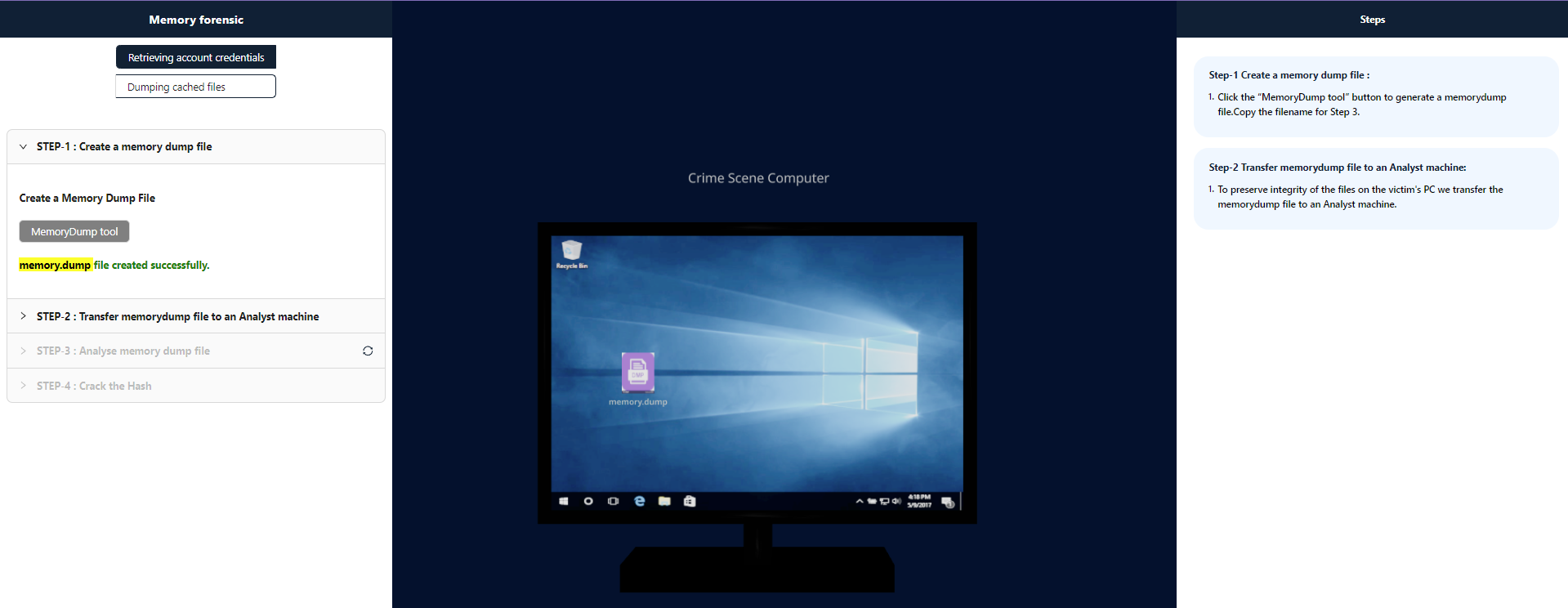
 Copy the filename highlighted in yellow color for Step 3.
Copy the filename highlighted in yellow color for Step 3.
Step-2 Transfer memorydump file to an Analyst machine:
To preserve integrity of the files on the victim's PC we transfer the memorydump file to an Analyst machine.

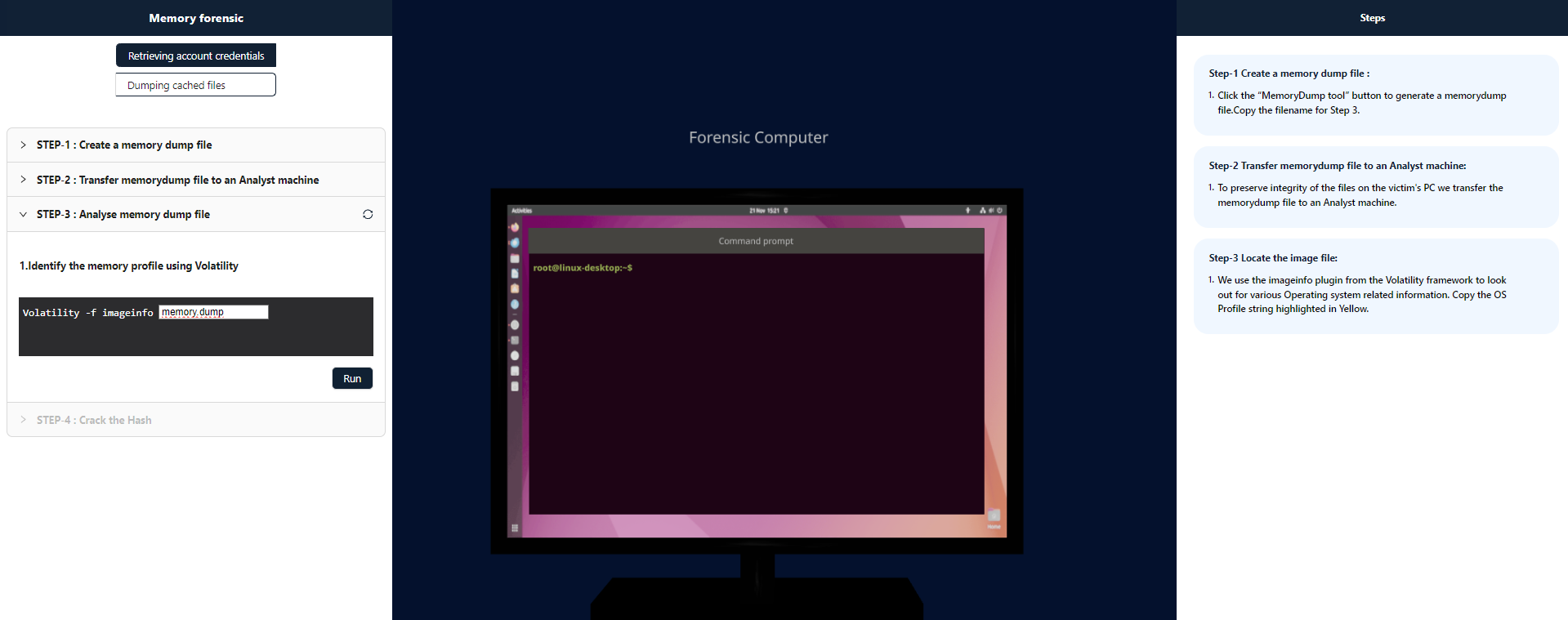
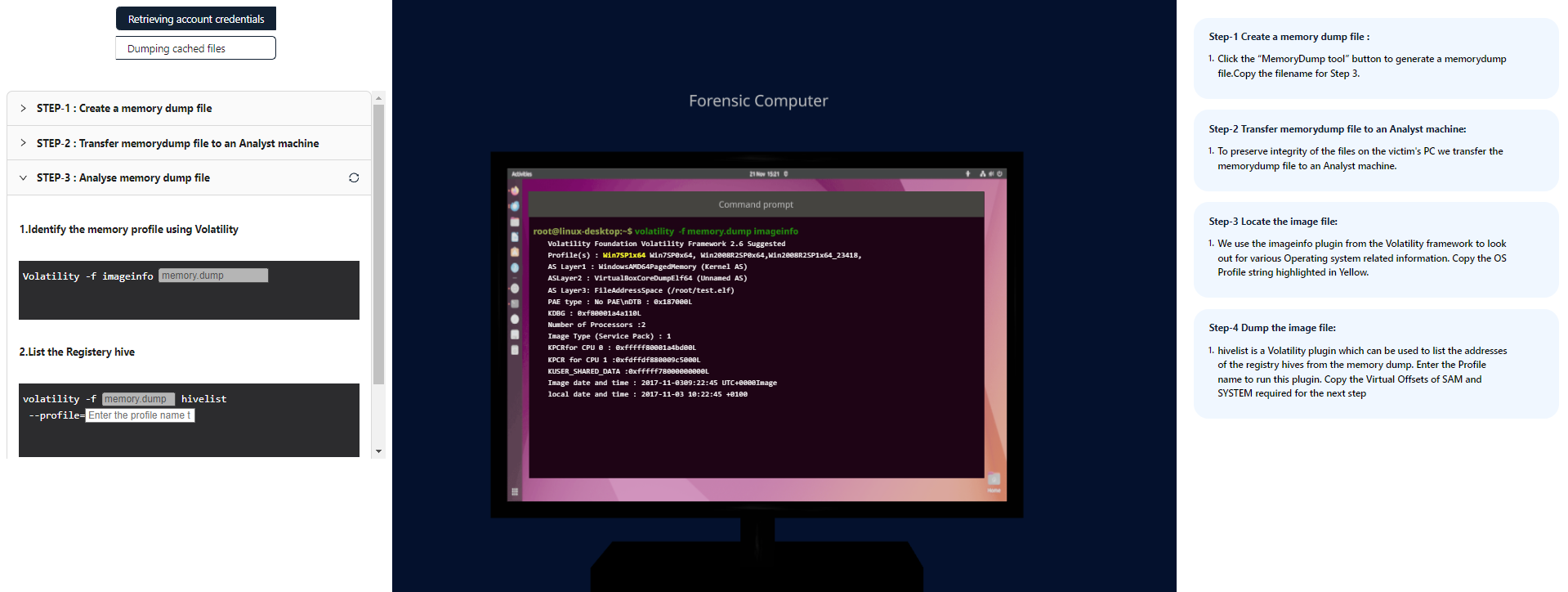
Step-3 Locate the image file:
We use the imageinfo plugin from the Volatility framework to look out for various Operating system related information. copy and paste the filename highlighted in yellow color from " Step-1:Create a Memory Dump File"
 Copy the OS Profile string highlighted in Yellow.
Copy the OS Profile string highlighted in Yellow.
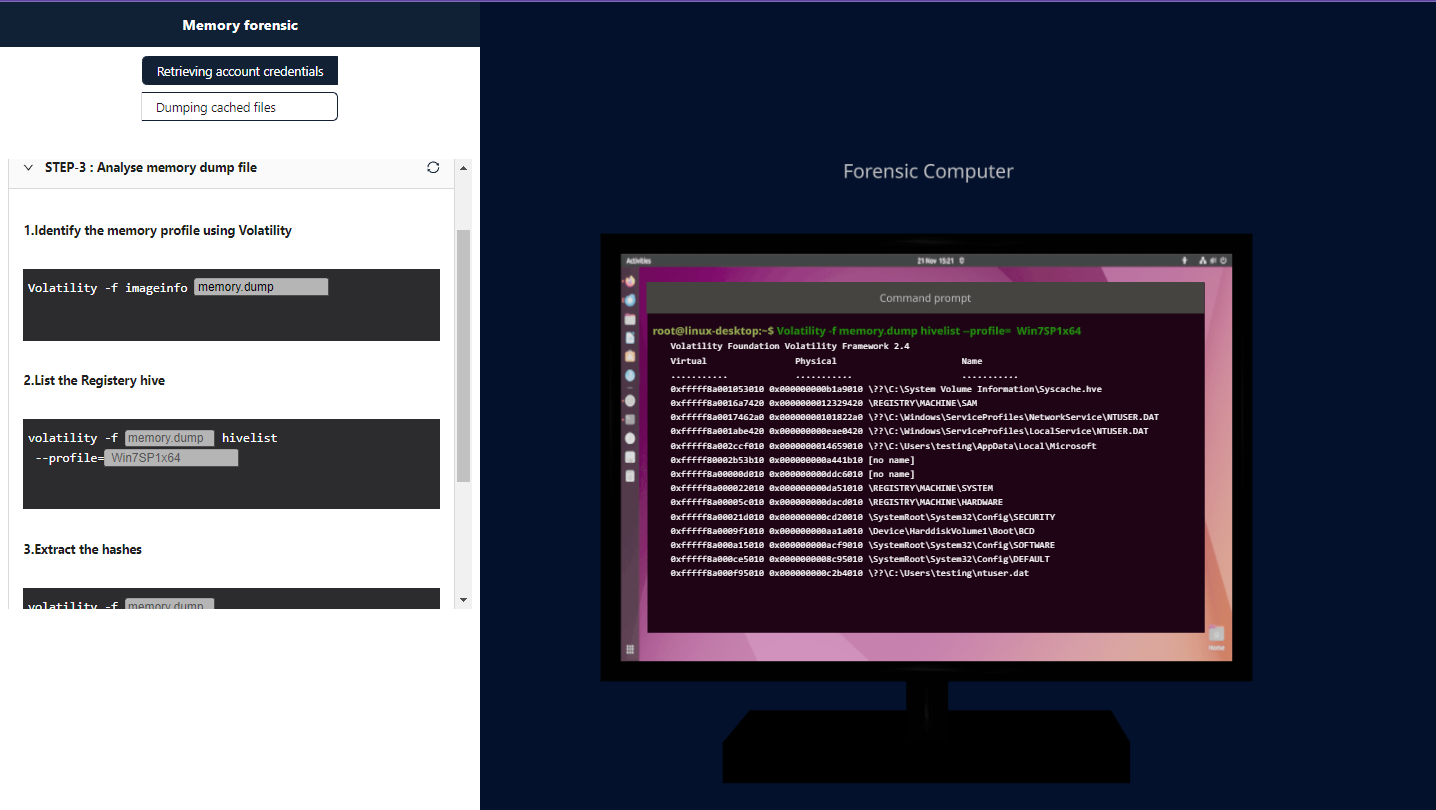
Step-4 Dump the image file:
Enter the Profile name to run this plugin. Copy the Virtual Offsets of SAM and SYSTEM required for the next step
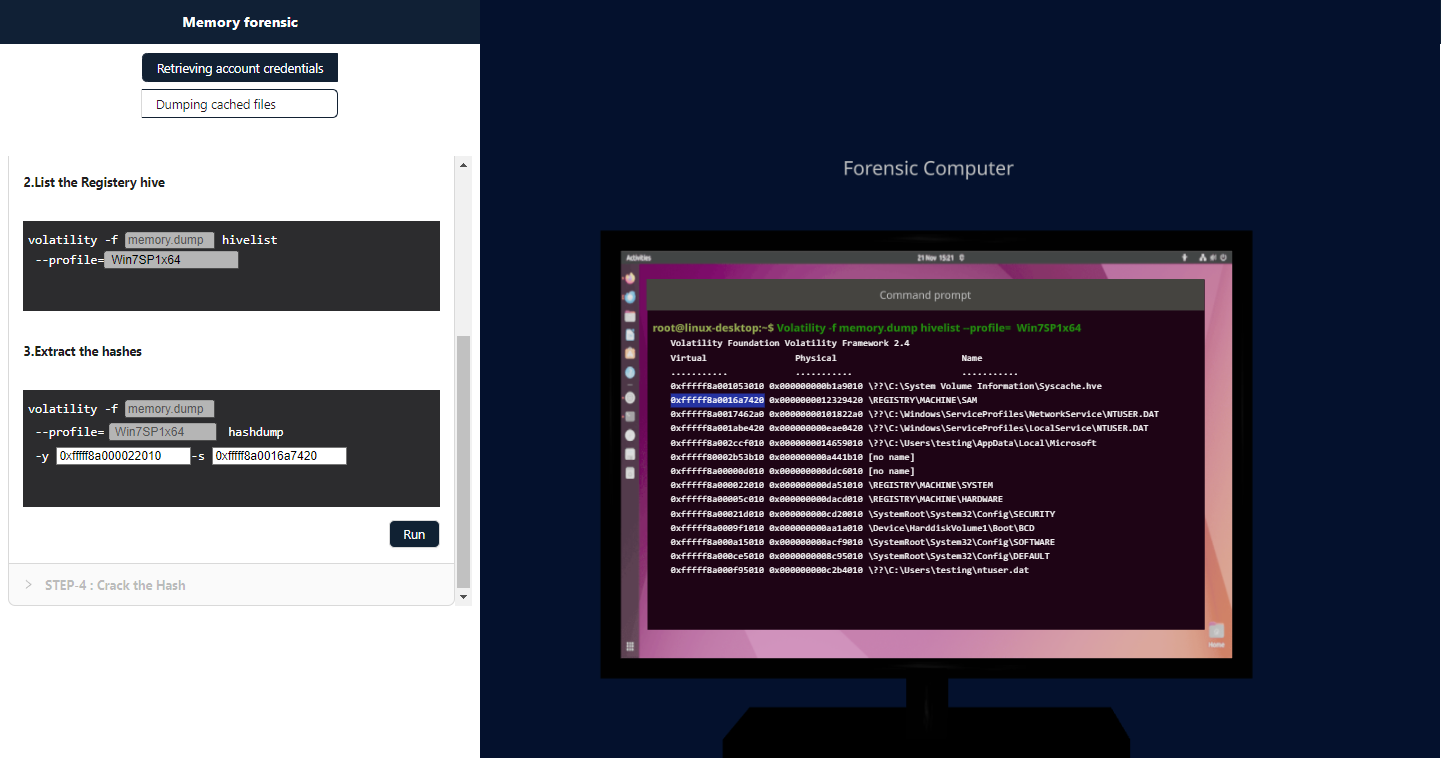
Step-5 : View the image file:
Paste the SAM and SYSTEM hive offsets in the box.
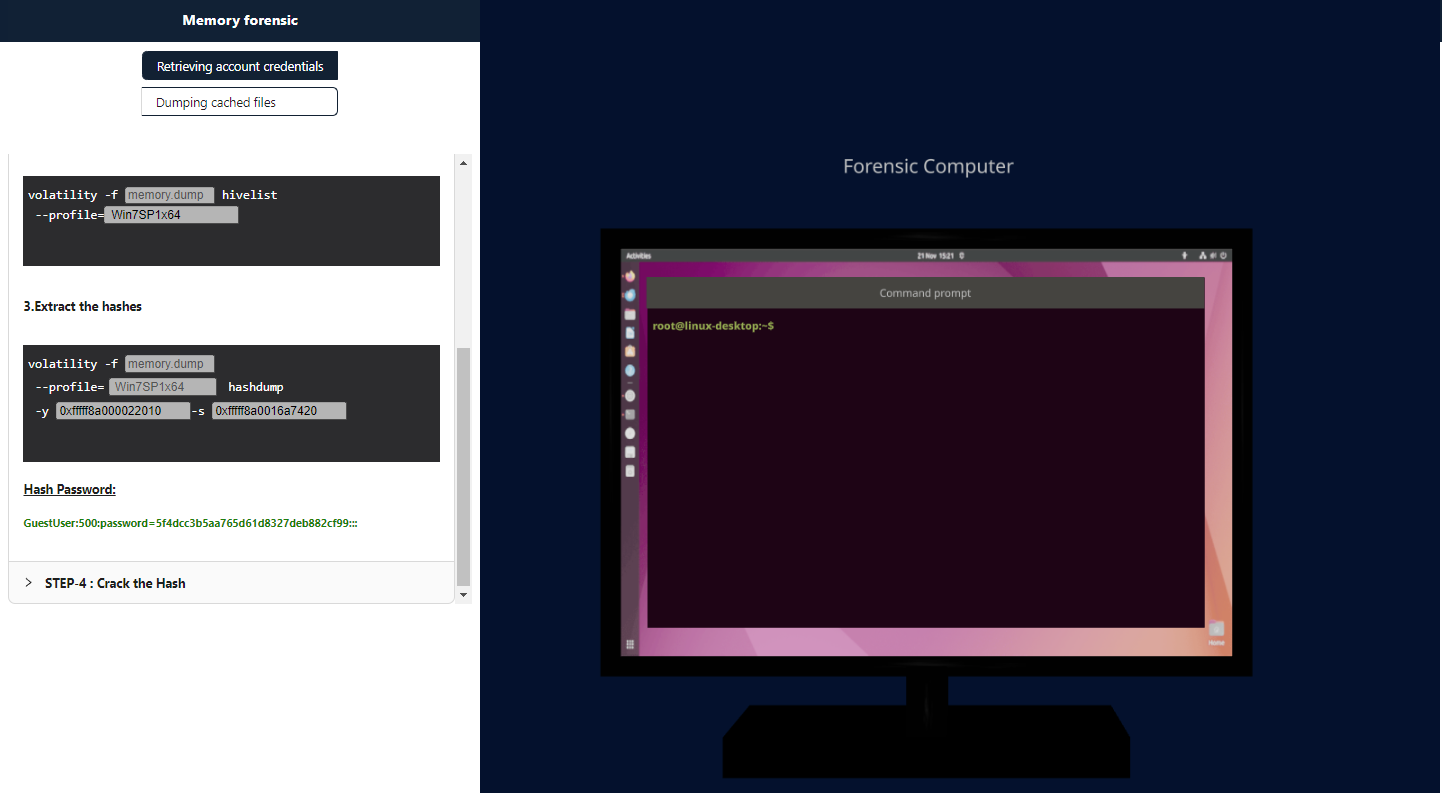
 The SAM and SYSTEM hive offsets are used as input in this step to run hashdump plugin which will print the password hashes. Copy the resulting hashes for the final step.
The SAM and SYSTEM hive offsets are used as input in this step to run hashdump plugin which will print the password hashes. Copy the resulting hashes for the final step.
Paste the hash to crack the password.
Cracked Password