Identifying Libraries and Network Connections in Malicious Binaries
Procedure
Step 1: Read the instructions displayed in the simulation and click the Start button to proceed to the next step.
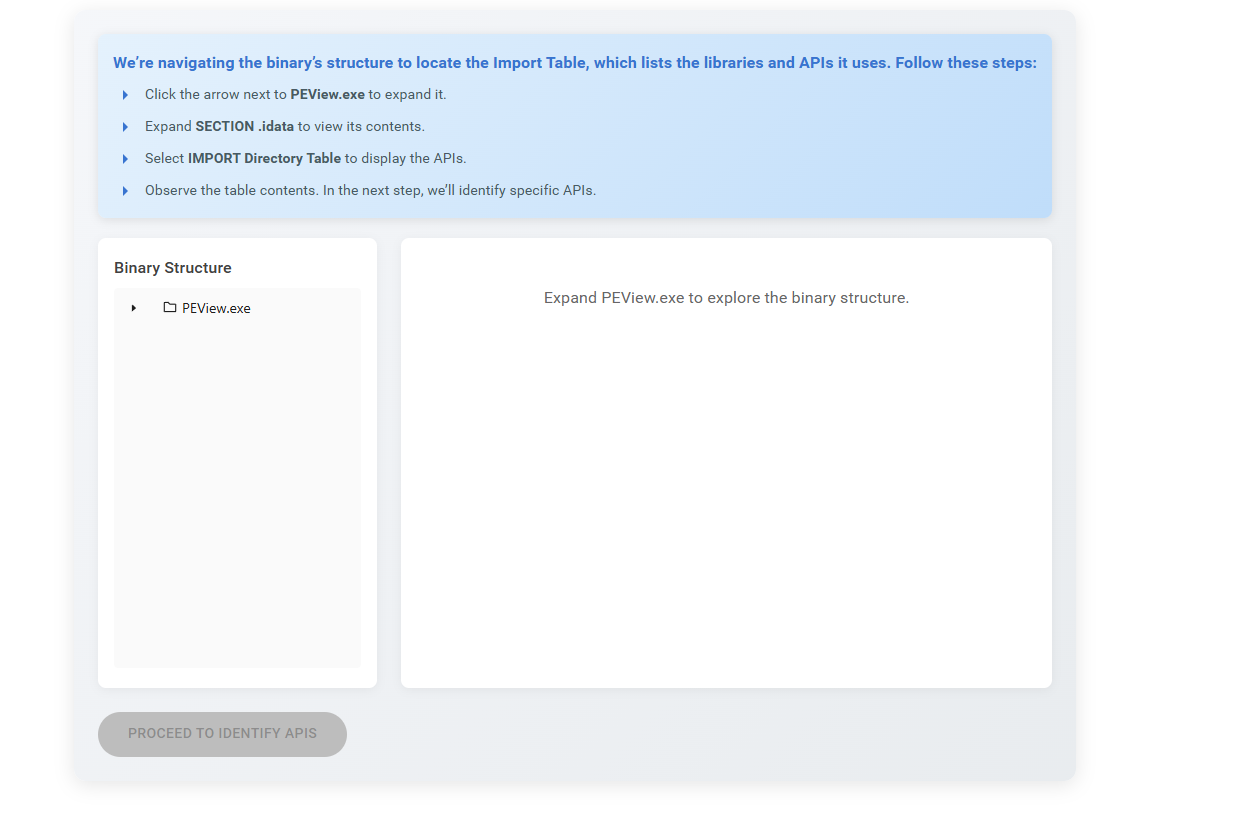
Step 2: Read the instructions carefully. Inspect the Import Table and navigate through the given directories as instructed.
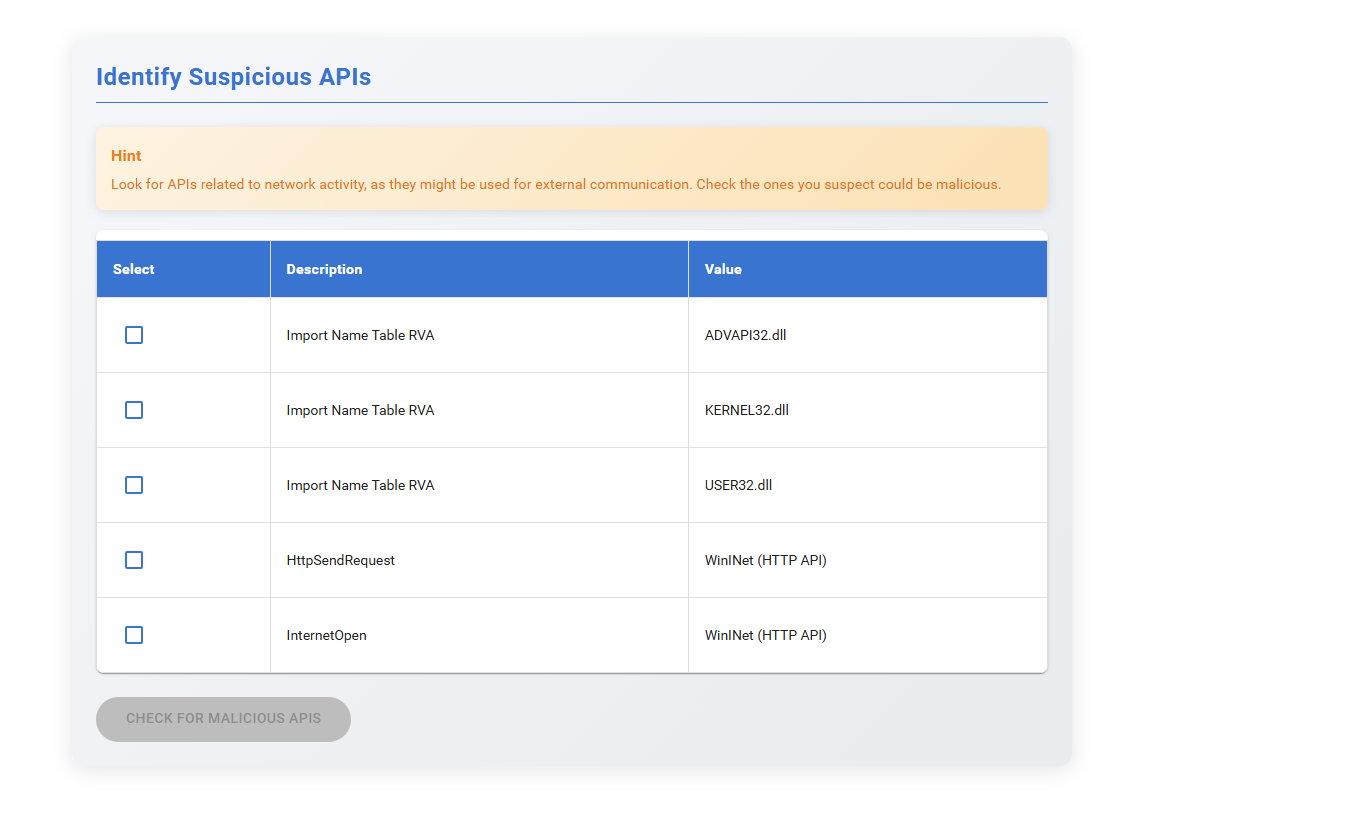
Step 3: Select the given APIs, identify the suspicious APIs, and click the Check for Malicious APIs button. Observe the results and read the explanation to understand how it works.
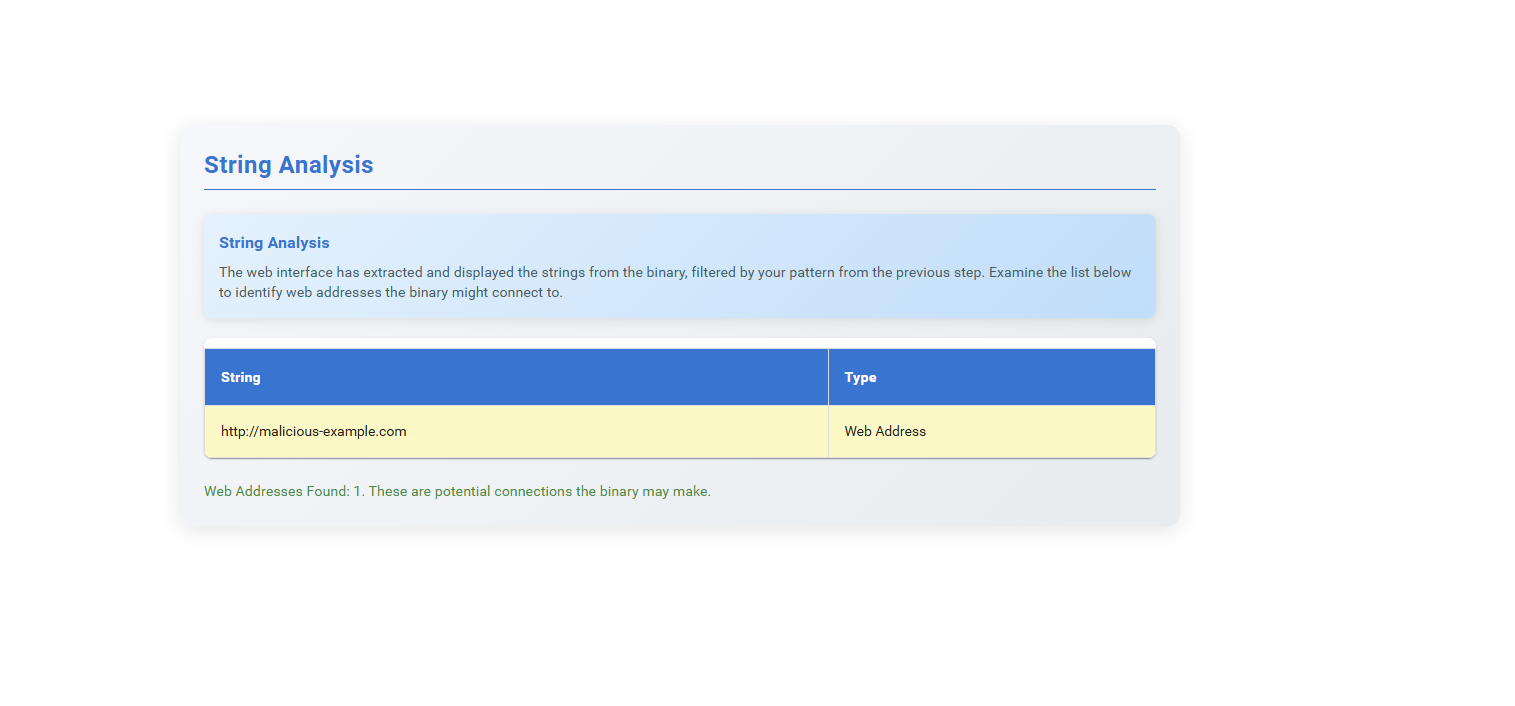
Step 4: Read the instructions, copy the given command, paste it into the terminal, and run it.
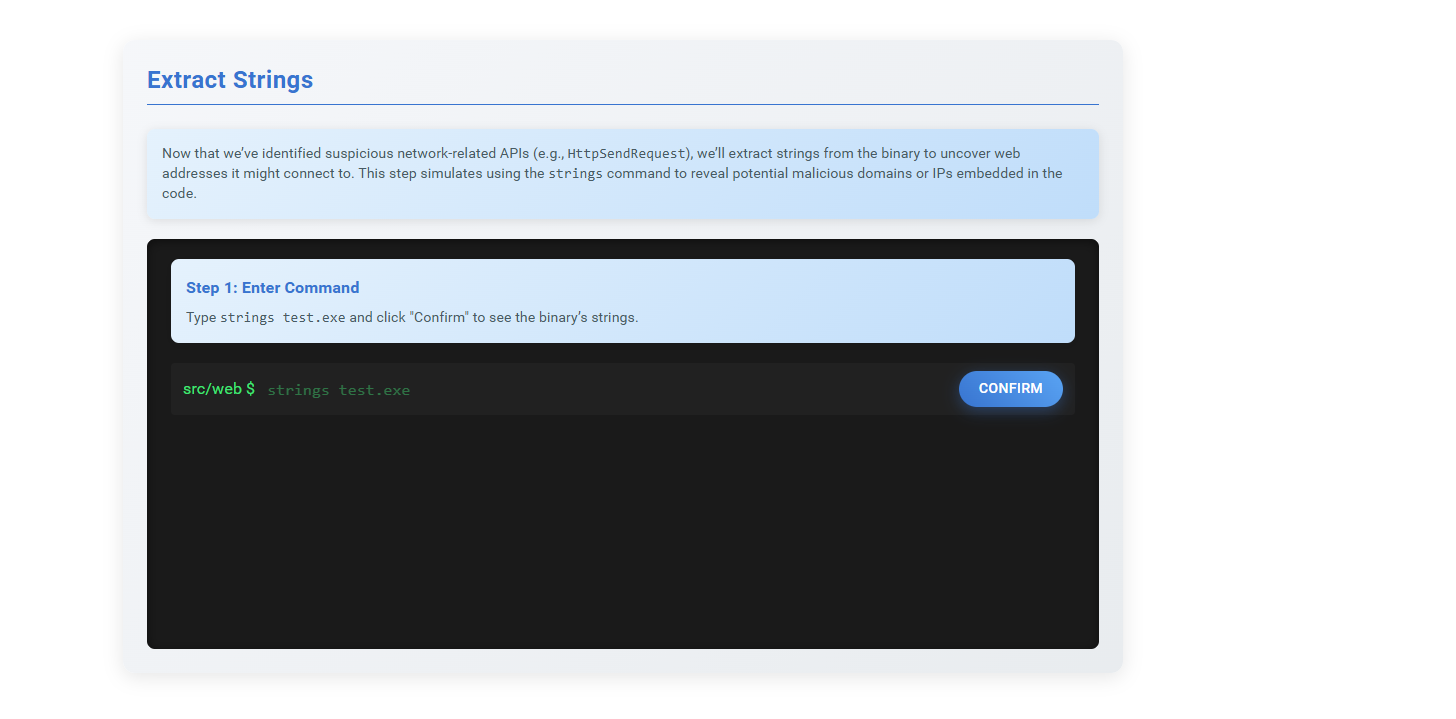
Step 5: Observe the results from the previous step.