Digital Signatures Scheme
For a very brief theory of digital signature schemes and their analysis, click here
Digital signatures are cryptographic mechanisms that provide authentication, integrity, and non-repudiation for digital documents and messages. Unlike handwritten signatures, digital signatures use mathematical algorithms to ensure that a document hasn't been altered and to verify the identity of the signer.
How Digital Signatures Work
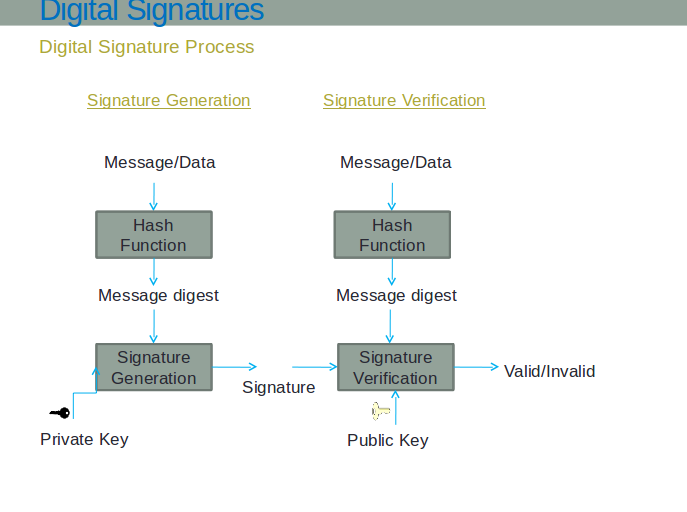
The digital signature process involves three main phases:
1. Hash Generation: The original message is processed through a cryptographic hash function (such as SHA-256) to create a fixed-size digest .
2. Signature Creation: The hash is encrypted using the signer's private key to create the digital signature .
3. Verification:
Recipients can verify the signature using the signer's public key to decrypt the signature and compare it with a freshly computed hash.
RSA-Based Digital Signatures
RSA (Rivest-Shamir-Adleman) is widely used for digital signatures due to its mathematical foundation:
Key Properties:
- Key Generation: Create a public-private key pair and
- Signing: Encrypt the message hash with the private key:
- Verification: Decrypt the signature with the public key:
RSA Security Assumption: The security of RSA digital signatures relies on the difficulty of the Integer Factorization Problem:
Trapdoor Function: RSA uses a trapdoor one-way function where:
- Easy direction: Computing is efficient
- Hard direction: Computing without knowing is computationally infeasible
Mathematical Representation
For RSA digital signatures:
Signature Generation:
Signature Verification:
Where:
- is the hash of message
- is the private key exponent
- is the public key exponent
- is the modulus ( for primes and )
RSA Key Generation Process:
- Choose two large prime numbers and
- Compute
- Compute Euler's totient function:
- Choose public exponent such that and
- Compute private exponent such that
Digital Signature Algorithm Steps:
Signing Process:
- Compute message hash:
- Generate signature:
- Send to verifier
Verification Process:
- Compute message hash:
- Decrypt signature:
- Verify: signature is valid if
Security Properties
Digital signatures provide three key security properties:
- Authentication: Verifies the identity of the message sender
- Integrity: Ensures the message hasn't been modified
- Non-repudiation: Prevents the sender from denying they signed the message
Key Size Considerations
The security of RSA digital signatures depends on key size and computational complexity:
| Key Size | Security Level | Factorization Complexity | Use Case |
|---|---|---|---|
| 512-bit | operations | Vulnerable to modern attacks | Educational only |
| 1024-bit | operations | Moderate security | Legacy systems |
| 2048-bit | operations | Currently recommended minimum | Production use |
| 4096-bit | operations | High security | High-value applications |
Security Growth: The security of an -bit RSA key against factorization attacks is approximately:
Performance vs Security Trade-off:
- Signature time: for -bit keys
- Verification time: Typically faster due to small public exponent (often )
- Key generation time: Increases significantly with key size due to primality testing
