Cross-Site Scripting Vulnerabilities
Procedure
Simulation Introduction
You have two simulated browsers. One represents you (the user), and the other belongs to Alice.
Both browsers will load a blog page, which allows you to post comments.
 Loading the Blog
navigate to the blog page
Observe the comments section where you can post your comments.
Loading the Blog
navigate to the blog page
Observe the comments section where you can post your comments.
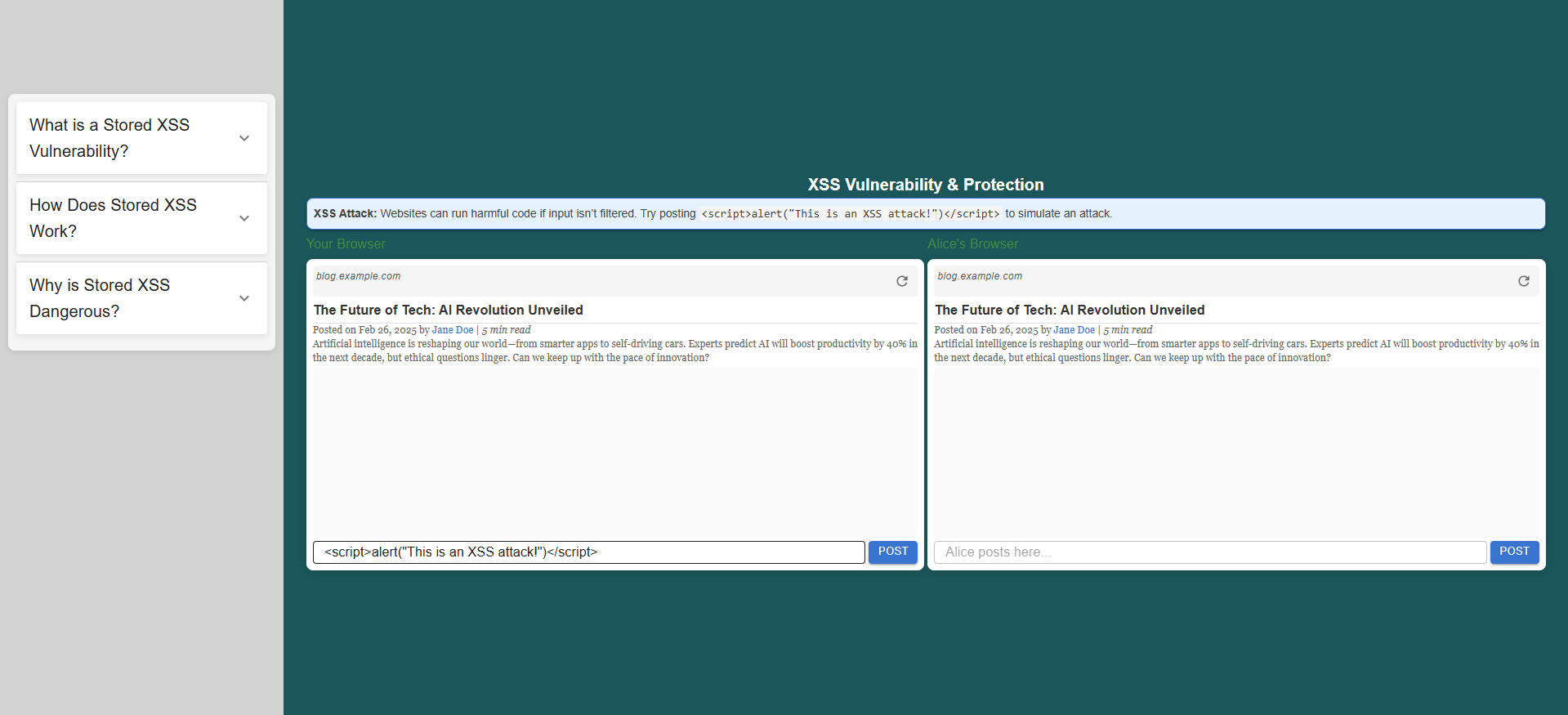
Introducing an XSS Payload
In your browser, type the following comment:
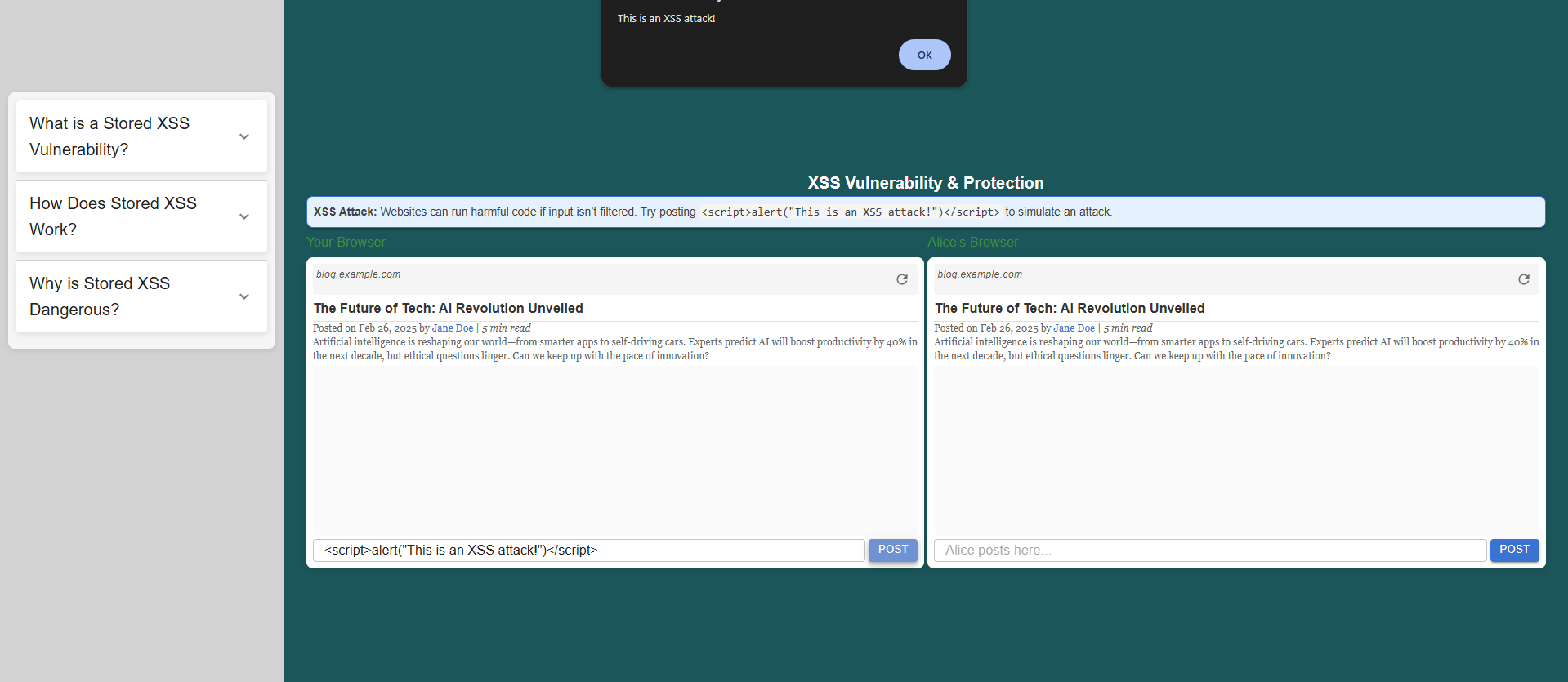
<script>alert("This is an XSS attack!")</script>
- Submit the comment.
Triggering the Alert
In your browser, observe that as soon as you submit the comment, an alert with the message pops up.
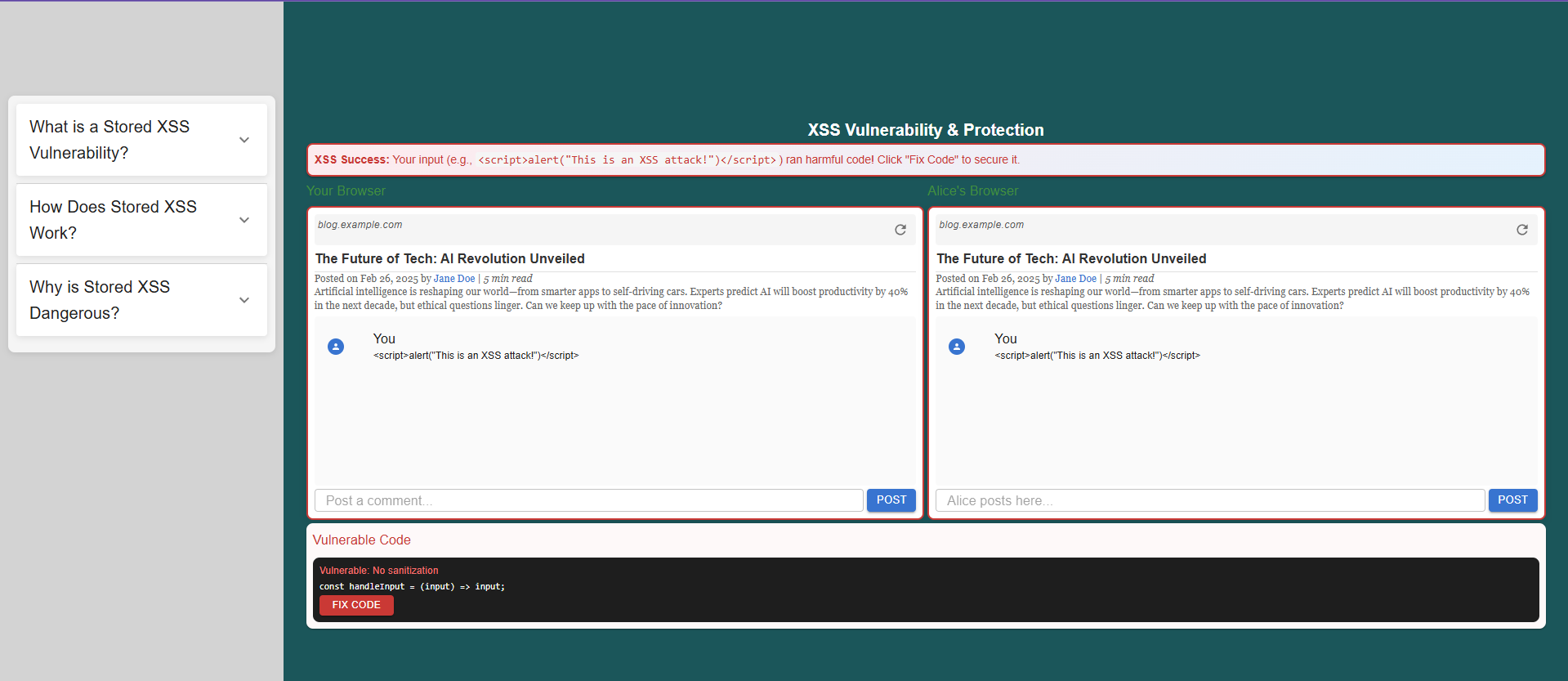
Storing the Payload
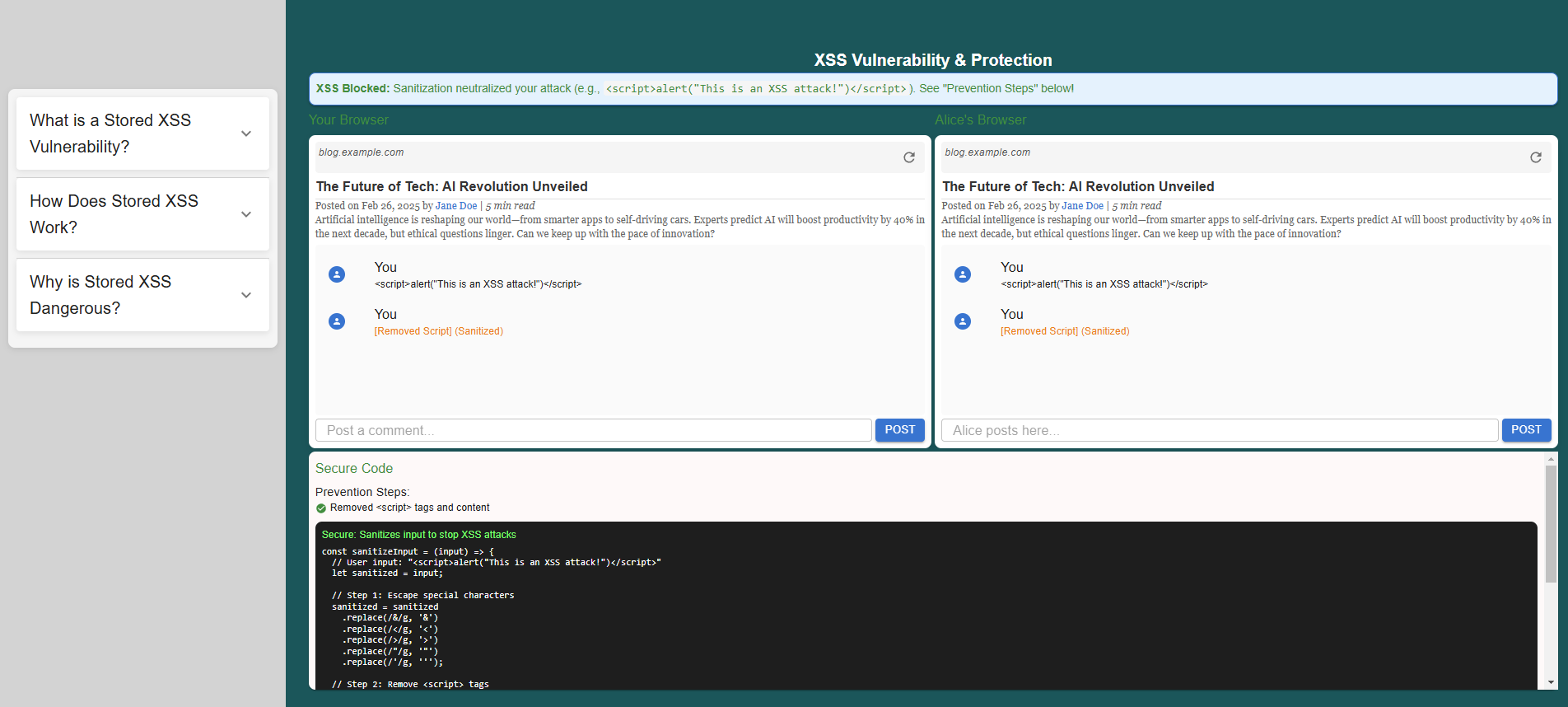
When you inject the XSS script, the application becomes vulnerable, allowing the malicious code to execute. Observe the code section where user input is not sanitized, leading to the vulnerability not being handled properly.
Click the "Fix Code" button to correct the vulnerability by properly adding sanitization to the input field. Observe the changes in the code and how it prevents the XSS attack.
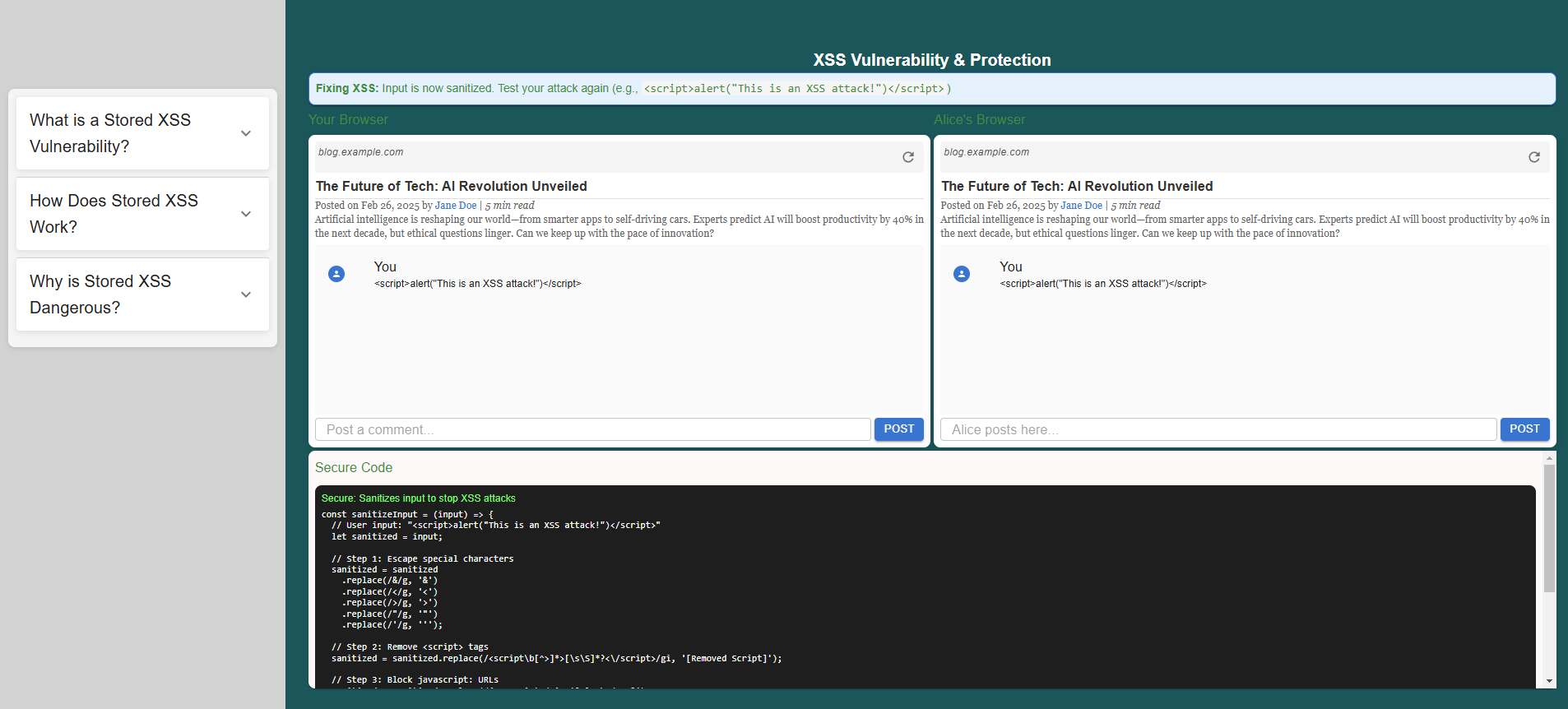
Step 6 - Preventing Stored XSS
To prevent stored XSS vulnerabilities,
Implement input validation and sanitization on the server-side to filter out or escape potentially malicious content.
Now, try entering the XSS script again and observe how input sanitization prevents the attack, ensuring the script is no longer executed.